Security of communications is, naturally, a concern for businesses looking to leverage a virtual service such as hosted PBX. When it comes to security with today’s telephony technology, it pays to be aware of the pitfalls.
With data and connectability through applications such as mobile Wi-Fi swirling all around us everywhere we go, business owners can be forgiven for thinking their communications can easily be hacked into and their commercially sensitive phone calls tapped.
Never have the worlds of business, commerce and industry had more opportunities to instantly connect and communicate with their audiences and stakeholders.
So what do you need to know when it comes to confronting and controlling security issues around your business communications?
- Change is a constant – One of the biggest security challenges is the fact that, like most things in life, the threats continue to change. Hacking is not just a habit for the bored, but a profession and in this age of disruption, assume anything is possible.Consider the case of this Perth VoIP provider targeted by a hacker who racked up 11,000 calls costing $120,000 over just 46 hours.While VoIP services ordinarily use the internet, opting for a dedicated private link that does not share an internet line will give you greater peace of mind, not to mention greater quality of service.
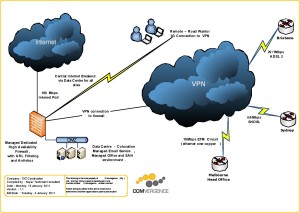
- Clouded comprehensions – The advent of the Internet and virtualisation have understandably opened up myriad opportunities for business. However, the cloud – to use one popular name for the technology – can also create security headaches for those who don’t fully understand its capabilities.In a basic sense, information passing over the internet can technically be monitored by third parties. This includes VoIP phone calls that unless encrypted with appropriate software or via a virtual private network (VPN) connection, effectively carry a risk of being accessible by unauthorised third parties, albeit needing the right equipment to listen in to phone calls.
- Security through obscurity – One increasingly common refrain is ‘security through obscurity’ (STO) – that is, relying on a lack of knowledge or awareness of any vulnerabilities or flaws in a system to effectively provide that security.
If you don’t want to take any chances, a VPN tunnel is one technology that allows for internet usage backed up by a variety of protocols that support private communications.
Hosted firewalls are another solution that more enterprises are using to secure their myriad online communications and transactions including IP voice, email and web-based applications involving or affecting day-to-day operations.
We’ve briefly touched on three ‘need to know’ aspects to security around hosted PBX – but what’s your take? Do you have a critical security issue or trend to share?
If so, please email us today with your suggestions, at sales@comvergence.com.au.